Perhaps you have a memorable password you’ve used many times before. It’s easy to remember, convenient, and feels secure. But is it really as safe as you think? Strengthening your password security is a small step that can make a big difference in safeguarding your data.
Let’s dive into the essentials of password security and ensure your passwords are robust and resistant to attacks. We’ve also developed an easy-to-use infographic powered by howsecureismypassword.net. This tool will help you evaluate your current passwords’ strength secure ones, and protect your data.
Why Password Security Matters
Passwords are the first line of defence against unauthorised access to your personal and professional accounts. A weak password is akin to leaving your front door wide open for intruders. Cybercriminals use sophisticated methods to crack passwords, and once they gain access, the consequences can be devastating, ranging from financial loss to personal identity theft. An estimated 22% of UK businesses and 14% of charities have experienced cyber crime in the last 12 months. Phishing is the most common type of cyber crime, affecting 90% of businesses and 94% of charities that experienced any form of cyber crime.
The Anatomy of a Strong Password
Creating a strong password doesn’t have to be complicated. Here are some key characteristics of a robust password:
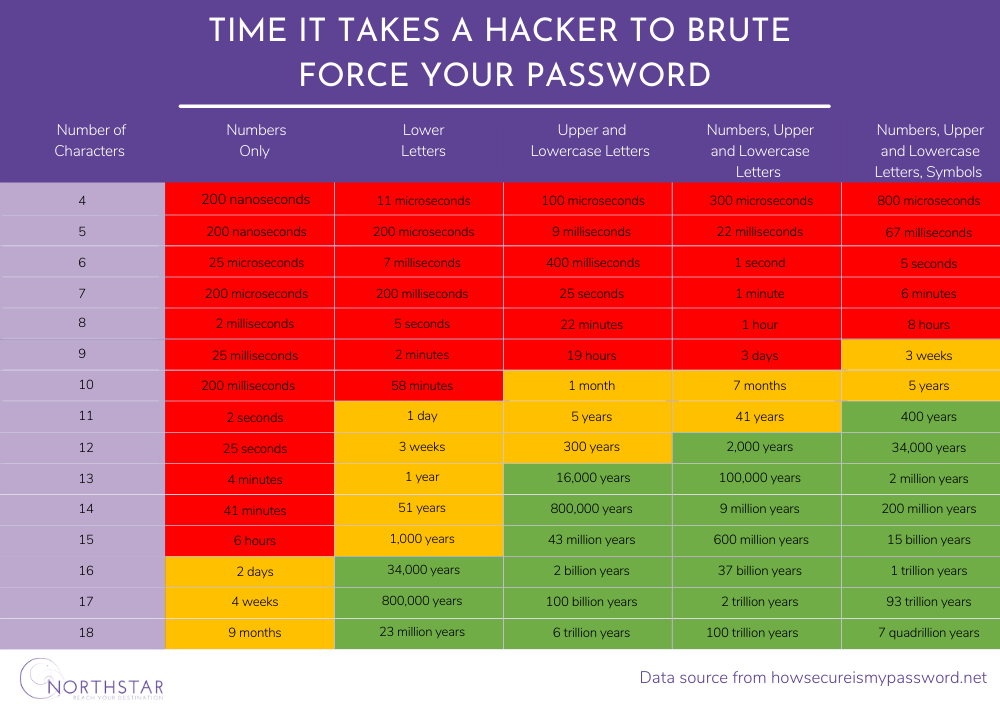
- Length: Aim for at least 12-16 characters. The longer the password, the harder it is to crack.
- Complexity: Use a mix of uppercase and lowercase letters, numbers, and special characters.
- Unpredictability: Avoid common words, phrases, or easily guessable information such as birthdays or names. Approximately 21% of users include their birth year in their passwords, and 18% use their pet’s name, both of which are easily exploitable by cybercriminals.
- Uniqueness: Use different passwords for different accounts to prevent a domino effect if one password is compromised.
PLEASE NOTE: DO NOT TYPE YOUR ACTUAL PASSWORD INTO AN ONLINE PASSWORD CHECKER. You can use the table to get an estimate of its strength.
Common Password Mistakes
Despite the awareness of the need for strong passwords, many people still fall into common traps. Here are some mistakes to avoid:
- Using Simple Passwords: “123456”, “password”, and “qwerty” are among the most frequently hacked passwords.
- Reusing Passwords: Using the same password across multiple sites increases the risk of multiple accounts being compromised if one is hacked.
- Neglecting Updates: Regularly updating your passwords can help protect against breaches and evolving cyber threats.
Tools and Best Practices
Here are some tools and best practices to help you manage and create secure passwords:
Password Managers
Password managers are essential tools for creating and storing strong, unique passwords for all your accounts. They can generate random, complex passwords and remember them for you, ensuring that you don’t have to rely on memory or risk using weak passwords.
Two-factor authentication (2FA)
Two-factor authentication enhances your security by requiring two forms of verification before granting access to your accounts. In addition to your password, 2FA involves receiving a unique code through a text message, email, or authenticator app. This extra layer of security ensures that even if someone manages to obtain your password, they still need the second factor to gain access.
Use a VPN
Internet service providers can track your online activity and device’s private IP addresses. The best way to hide your activity and details is to use a VPN (a virtual private network) instead of connecting to private wifi.
Get Identity Theft Protection
If someone cracks your password, there is no way of stopping someone from using your personal information for identity theft. Instead, you can use identity theft protection software to monitor criminal and financial use of your personal information.
Use Antivirus Software
Antivirus software scans computers, phones and tablets for malware, viruses, ransomware, spyware and other cyber threats trying to steal your password on your device.
Cyber Security Assessment With Northstar
Here at Northstar, we understand that the foundation of a robust cyber defence strategy begins with a thorough understanding of your current security posture. Our comprehensive Cyber Security Assessment is designed to meticulously evaluate the security of your IT systems and passwords, identify vulnerabilities, and provide actionable insights to fortify your defences.
By understanding the importance of password security and implementing these best practices, you can significantly reduce the risk of unauthorised access to your accounts. Stay vigilant, stay updated, and ensure your passwords are as strong as possible.
If you have any concerns about cyber security or password management, then contact Northstar today.